Almende works on R&D projects to turn ambitious ideas into real-world technology that delivers measurable impact.
By partnering with us, you gain access to a dedicated team with deep technical expertise, a proven track record, and the ability to turn complex concepts into practical technical solutions tailored to your needs.

Our portfolio below showcases how we’ve helped accelerate innovation and solve real challenges across the innovation themes Smart Buildings, Smart Health, Smart Robotics, and Smart Societies.
Explore our projects to see the value we can bring to your next research or innovation project.
View all the projects or only projects in a specific theme by filtering the list on a tag. Click on any project slide to visit the dedicated project page with more details about the project.






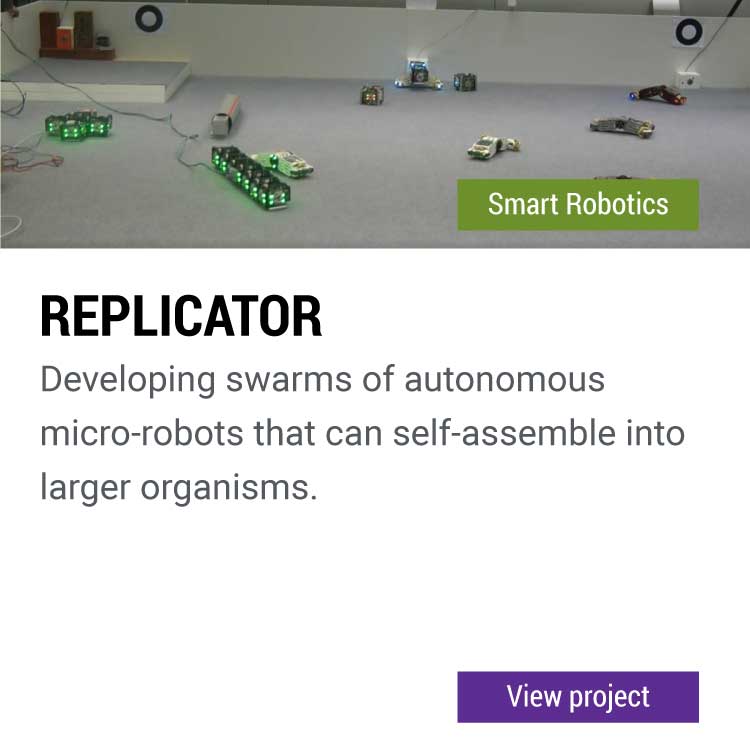

Are you interested to cooperate on a research project? Get in touch with us!
Fill in the form and one of our research consultants will get in touch with you.